In this post, let us see how to reset a password and make the account active in NSX-T.
Remember that this account was created using API as you can’t create local accounts using NSX-T UI. My NSX-T version is 3.2.2.x.x
Back Story: one of the local accounts which I created for skyline collector in our NSX-T environment password was expired. Hence, I had to use the API to Update the User account password and status to make the account ACTIVE again.
Use an API Editor like Postman to get the required data as shown in the screenshot below:
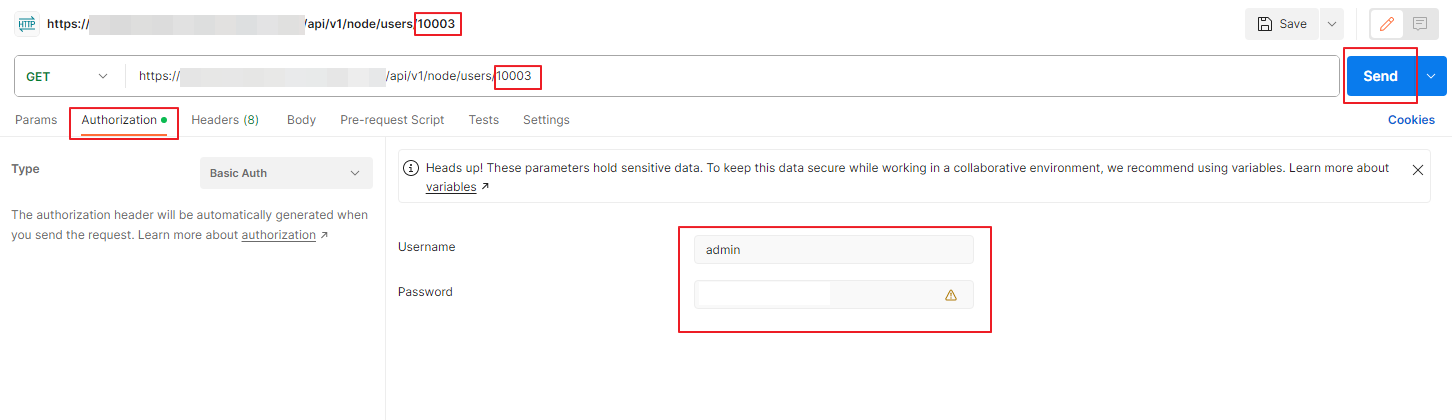
In the GET field, you will be providing the following code.
https://<nsx-t hostname/IP-address>/api/v1/node/users/<user-id>You can get the user-id pretty easily by going to System and User Management in NSX-T UI and get the user-id. In the above example my user-id is 10003. Then go to the Authorization tab and provide the username and password of the NSX-T Manager where you want to make these changes. Then click on Send option to get the required info.
you will get the data as the below screenshot.

You will observe that the last password has been changed 95 days ago, password change frequency is every 90 days, status is password expired and the actual username (in this case its labprdsky_nsxt)
you will have to change the body of this into the below values
{
"full_name": "Guest User1",
"last_password_change": 1,
"password_change_frequency": 999,
"old_password": "<old_password>",
"password": "<new_password>",
"password_reset_required": false,
"status": "ACTIVE",
"userid": 10003,
"username": "labprdsky_nsxt"
}You can change the password_change_frequency from 0 to 9999, you will have to provide the old password which is expired and the new password for this account and change the status to ACTIVE.
We will copy the above code into the body of the next PUT statement as shown below

Change the GET to PUT and insert the above code with the changed values in the body as the screenshot shown above and click on Send
The output will be displayed as below

{
"full_name": "Guest User1",
"last_password_change": 0,
"password_change_frequency": 999,
"password_reset_required": false,
"status": "ACTIVE",
"userid": 10003,
"username": "labprdsky_nsxt"
}The above output is in code form in case you want to copy it.
Now you can do the above GET command to get the status of the user and you will see that this account shows as active and the password change frequency is now 999 days.
Final output for GET for that user 10003

Hope this writeup helped you to unlock and reset the password of an local user created using API in NSX-T.

