These are some of the features added/enhanced for On-prem usage with NSX 4.1.1 version
Layer 2 Networking
- Filter VLAN on VLAN Transport Zone: It is now possible to define a list of VLANs authorized for a given VLAN-based transport zone, which prevents NSX tenants from using some VLANs already used for general connectivity in the datacenter.
- ESX Observability Enhancements: NSX API now offers statistics for ESX overlay, ESX distributed routing and switch security (IP discovery and spoof guard) modules which were only available through the CLI in previous releases. This gives more options to monitoring the NSX modules running on ESX.
- Enhanced Data Path (EDP) now supports the following improvements:
- Support of double overlay encapsulation traffic coming from VMs and containers to a host switch, offering better performances to Antrea deployments.
- Support of MAC and VLAN filtering, which allows a physical NIC driver to program (MAC, VLAN) pair to physical NIC Rx queue.
- Optimization of flow cache for Geneve overlay traffic reducing the impact of large numbers of flows on forwarding performance.
Layer 3 Networking
IPv6 TEP (tunnel end point) support for Transport Nodes: This release introduces support for IPv6 TEP (tunnel end point) with Geneve encapsulation for Transport Nodes (Edge Nodes and ESXi hosts). With this feature, you can create overlay Transport Zones using IPv6 as the underlay transport protocol.
DPU-based Acceleration
NVIDIA BlueField-2 (100Gbps) is now supported
Edge Platform
- Bare Metal Edge supports Intel 810: expands the list of supported NICs with 25Gbps/100Gbps Intel NIC.
- Disabled Flow Cache Alarm on Edge Node: With VMware NSX 4.1.1, if the flow cache is disabled on Edge Transport Node, NSX triggers an alarm. This ensures Edge Transport Nodes can deliver the best performances.
- Packet drop alarm: The alarm shows more specific information about packet drops, providing more granular information.
- Maximum supported cores for Bare Metal Edge: With VMware NSX 4.1.1, the Bare Metal Edge node can have up to 80 cores that will maximize the performance of the Edge node.
Physical Server
Added support of Windows 2012R2 OS for the Physical server transport node.
Container Networking and Security
- Scale Improvements for TKGi: NSX 4.1.1 brings scale parity for TKGi customers shifting from Manager Mode APIs to the declarative Policy APIs.
- Support for more than 1000 OpenShift routes with NCP 4.1.1.
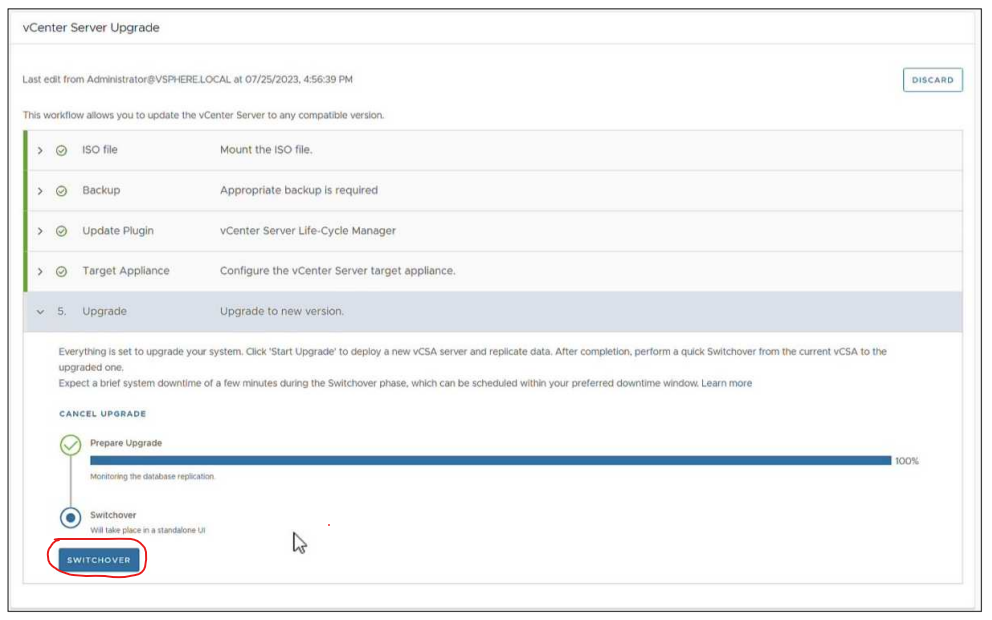
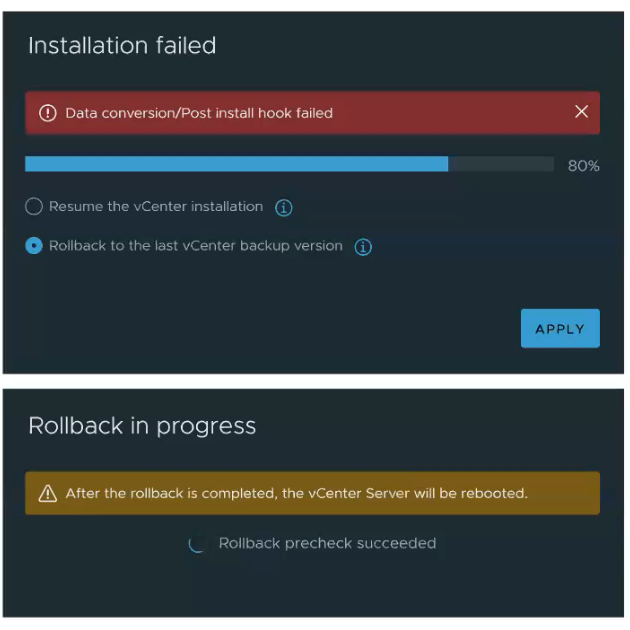
Installation and Upgrade
- Run NSX pre-upgrade checks at any time and independent of the upgrade process. Check upgrade readiness and fix any underlying issues ahead of time, and use your maintenance window for actual upgrades. Benefit from latest pre-checks added dynamically by NSX.NOTE: While this capability allows you to run pre-checks in advance, they do need to be mandatorily run again before starting an NSX upgrade. This is to ensure an accurate and latest assessment of your deployment right before upgrade.
- NSX Federation now supports the same upgrade interoperability of N+2 (N = minor version number in product series) as NSX on-premises.
- Reduced downtime in rolling upgrade of NSX Manager cluster.
- Revamped NSX Upgrade UI for better performance. Additional user experience enhancements in the NSX upgrade process.
- Search <uuid> command is added to help to search the resource details using UUID to identify IP Address, Host Name, Display Name and Resource Type.
- The NSX Manager UI now displays a banner when the NSX Manager is deployed by VMware Cloud Foundation. The NSX Upgrade splash page also reminds you to upgrade NSX from SDDC Manager when NSX is deployed by VMware Cloud Foundation.
Operations and Monitoring
- LTA support on ESXi ENS Fastpath
- Counter actions is introduced in this release and available on API, which enables users to trace the ENS fastpath and slow path traffic on the port.
- Status metrics in string format can now be persisted in NAPP as Time-Series metrics, for example: cluster status metric shows the health of the NSX Manager cluster, and has values in string format i.e., stable/unstable/degraded, which can now be persisted in NAPP. This will allow you to monitor the status metrics which are strings over a period of time with historical context.
- Online Diagnostic System
- Thirteen new runbooks are added in this release to help with troubleshooting across Edge, Host and NSX Manager. See the Administration Guide for more information.
- NSX CLI Enhancements
- More than one filter can be applied on the CLI commands to filter the data, which is helpful to filter the large output.
- New modifiers sed, awk, uniq are supported to filter and format the CLI output.
- From the central CLI, users can now execute the commands on remote CLI using IP Address, Host Name and Display name. This provides flexibility to execute CLI commands on remote nodes using any of these identifiers.
- The search <input-str> CLI command is added. This command can be used to get information such as the IP address, display name, resource type for any <input-str>. Along with the search string, resource-type parameter can be added to filter the resource type.
- Transport Node APIs are updated to provide various details to aid in monitoring.
- Transport Node Status API
- MP connection status can be retrieved real time using source=realtime field in the API call.
- For CCP connection, the status description field is added. This describes the reason for the disconnection and last status changed time field shows when the status was updated.
- For pnic status, details of pnics that are down and last status change are added.
- For cfgagent and opsagent, component and last status change fields are added.
- Aggregated status now has status description, which shows the reason why aggregated status is not up and last aggsvc heartbeat, last status changed time added shows when the mp connection was active and status was updated.
- PNIC bond Status API
- Pnic bond details and type field reflecting whether it’s used for NSX or non-NSX are added.
- Transport Node Status API
VPN
With NSX 4.1.1 you can now enable the allocation of more cores for VPN services
Platform Security
Local User Account Management: Adds an NSX API for listing local user accounts on NSX appliances (NSX Manager, NSX Edge, NSX Application Platform, NSX Cloud Service Manager).
IPv6 TEP (tunnel end point) support for Transport Nodes
This release introduces support for IPv6 TEP (tunnel end point) with Geneve encapsulation for Transport Nodes (Edge Nodes and ESXi hosts). With this feature, users can create overlay Transport Zones using IPv6 as the underlay transport protocol.
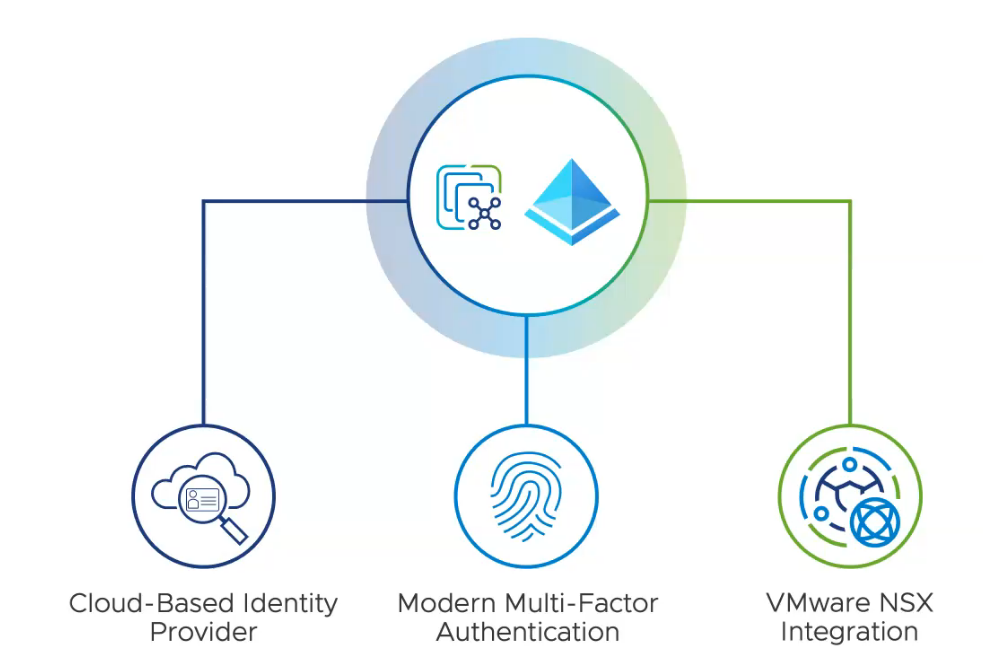
Here are some of the features with NSX which are used to connect with NSX+ and for the Cloud model —–
- Securely connect to VMware NSX+ Services: NSX 4.1.1 provides on-premises NSX Manager deployments to securely connect to NSX+ Services. Details of NSX+ Services are available in the NSX+ Release Notes.
- Cloud Consumption Model with NSX VPCs: New NSX VPC allows self service consumption for networking, security and services through on-demand isolated environment aligned to Cloud standard consumption. It offers a second level of tenancy below Project, with a streamlined UI and API to allow teams to easily deploy networking and security in the Cloud environment.
- Multi-tenant Distributed IDS/IPS: Distributed IDS/IPS now offers multi-tenant consumption with the ability to configure it under Projects. It allows multiple users to apply IDS/IPS rules to their own VMs without risks of overlap.
Reference: VMware NSX 4.1.1 Release Notes